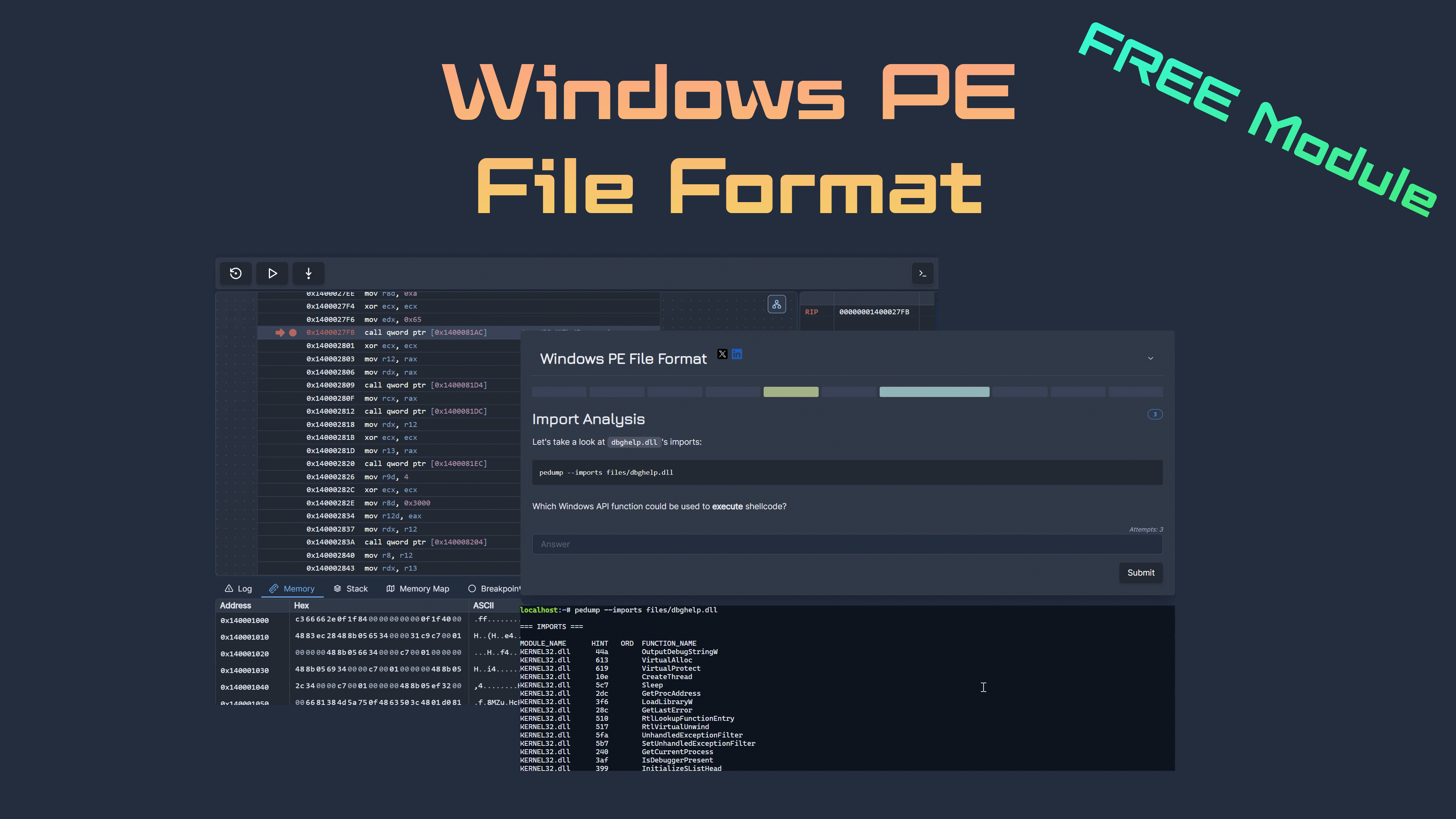
This module is designed to familiarize you with the Portable Executable (PE) file format and demystify its structure. While PE files might seem complex at first, they follow a logical and well-documented structure that becomes intuitive with practice. The format itself isn't difficult to understand. It's simply a matter of knowing where to look and getting lots of hands-on experience analyzing real samples.
Our goal is to equip you with the ability to quickly identify different sections and components of a PE file during analysis. More importantly, you'll learn what the PE file format offers to attackers and how adversaries leverage its features for malicious purposes. By the end of this module, you'll be able to recognize common malware patterns like packing, DLL side-loading, and resource-based payload delivery just by examining the PE structure with tools like pedump.
Sign up to access this content

