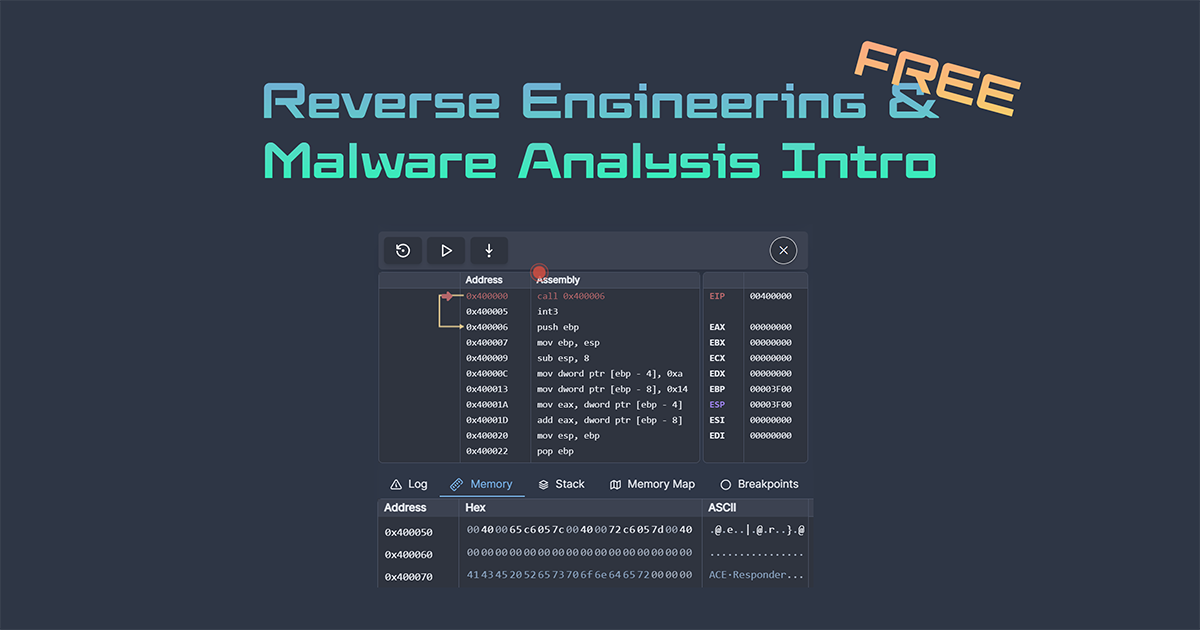
This hands-on module walks you through real reverse engineering challenges using our in-browser debugger.
- No VM
- No malware downloads
- No setup
You'll work with code samples designed to show you how assembly works, stepping through instructions one at a time, inspecting registers and memory, and solving puzzles designed to teach you how programs work at the assembly level. Each exercise builds on the last, gradually introducing new concepts like function calls, loops, conditional logic, and data manipulation. By the end, you'll be comfortable reading x86/x64 assembly and understanding program flow.
The module is designed for complete beginners. You don't need prior experience with assembly or low-level programming, just curiosity and persistence.
Sign up to access this content

